The best free & open source container tools
Manage containers, pods, and images with Podman. Seamlessly work with containers and Kubernetes from your local environment.
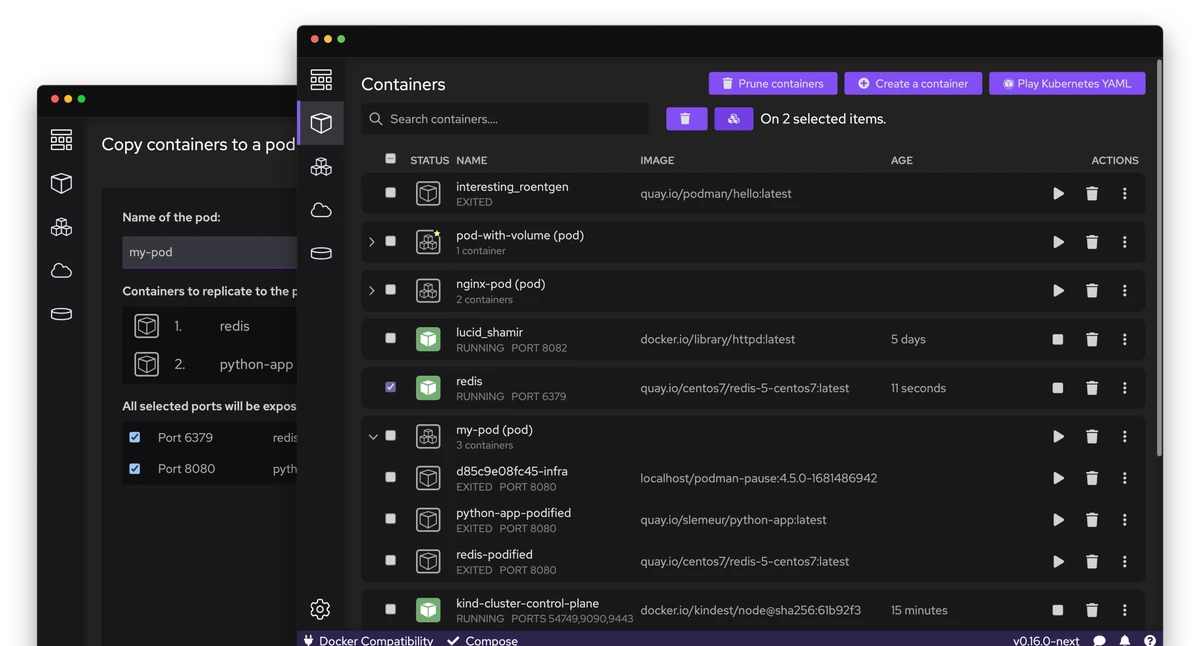
Fast and light.
Daemonless, using the fastest technologies for a snappy experience. Our UI is reactive and light on resource usage and won't drag you down.
Secure.
Rootless containers allow you to contain privileges without compromising functionality. Trusted by US government agencies for secure HPC at scale case study.
Open.
Podman is open source first and won't lock you in. Podman Desktop can be used as one tool to manage all your containers, regardless of container engine - even if you don't use Podman as your container engine.
Compatible
Compatible with other OCI compliant container formats including Docker. Run your legacy Docker containers (including docker-compose files) on Podman. Learn more
Kubernetes Ready
Create, start, inspect, and manage pods. Play Kubernetes YAML directly with Podman, generate Kubernetes YAML from pods, and deploy to existing Kubernetes environments.
A growing set of compatible tools
Kind's ability to run local Kubernetes clusters via container nodes includes support for Podman
Kind's ability to run local Kubernetes clusters via container nodes includes support for Podman
Kind's ability to run local Kubernetes clusters via container nodes includes support for Podman
Kind's ability to run local Kubernetes clusters via container nodes includes support for Podman
Latest Podman News
 Why does SELinux container policy allow all Linux capabilities?
Why does SELinux container policy allow all Linux capabilities?I recently had a discussion in a container-selinux issue on why we allow certain capabilities by default for containers. The conversation is around DAC_OVERRIDE, a Linux capability which allows privileged processes, usually...
 Why does SELinux container policy allow all Linux capabilities?
Why does SELinux container policy allow all Linux capabilities?I recently had a discussion in a container-selinux issue on why we allow certain capabilities by default for containers. The conversation is around DAC_OVERRIDE, a Linux capability which allows privileged processes, usually...
 Why does SELinux container policy allow all Linux capabilities?
Why does SELinux container policy allow all Linux capabilities?I recently had a discussion in a container-selinux issue on why we allow certain capabilities by default for containers. The conversation is around DAC_OVERRIDE, a Linux capability which allows privileged processes, usually...
 Why does SELinux container policy allow all Linux capabilities?
Why does SELinux container policy allow all Linux capabilities?I recently had a discussion in a container-selinux issue on why we allow certain capabilities by default for containers. The conversation is around DAC_OVERRIDE, a Linux capability which allows privileged processes, usually...